OKTA
4me has an Okta Verified Provisioning (SCIM) Certification.
Features
The following provisioning features are supported:
- Push New Users: new users created through OKTA will also be created in 4me.
- Push Profile Updates: updates made to the user’s profile through OKTA will be pushed to 4me.
- Push User Deactivation: deactivating the user or disabling the user’s access to the application through OKTA will deactivate the user in 4me.
Remark: deactivating a user in 4me means the user will not be able to access 4me anymore and the user cannot be selected anymore in the service desk console by a service desk analyst. But be aware that all the user’s data will still be kept in 4me. When a user with the same email address is activated in Okta, the same 4me user record will be activated again with the link to the existing tickets.
- Push Groups: group memberships can be pushed to 4me.
Remark: groups, for which you want the membership to be pushed from Okta to 4me, need to be predefined as a 4me organization.
Prerequisites
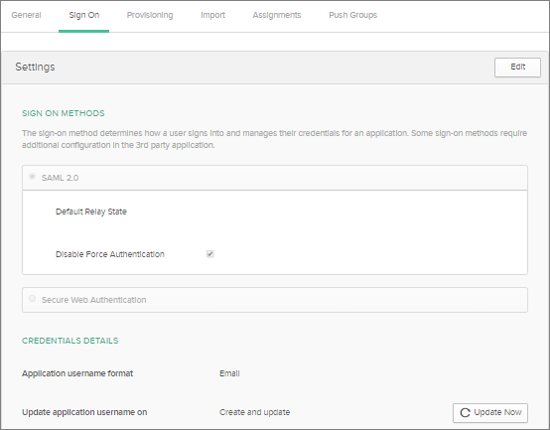
Before you configure provisioning for 4me, make sure you have configured the General Settings and any Sign-On Options for the 4me app. Make sure the ‘Application username format’ is defined as ‘Email’.
Configuration Steps
Configure your Provisioning settings for 4me as follows:
4me Connection Information
Get the 4me SCIM endpoint and 4me SCIM bearer token via these instructions: 4me connection information.
Remark: you need to be the account owner of the 4me account to access these data. If you are not the account owner, ask the account owner for this info.
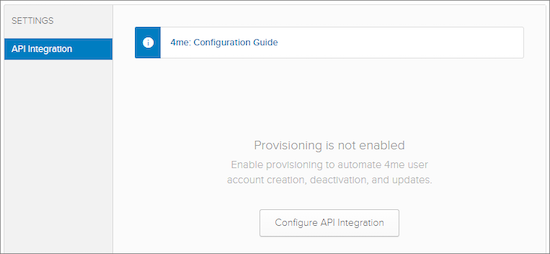
Open the 4me App and Configure API Integration
- Go to the Provisioning Section
- Click on the ‘Configure API Integration’ button
- Check the ‘Enable API integration’ box
- Fill in the Base URL (your 4me SCIM endpoint)
- Fill in the OAuth Bearer Token (your 4me SCIM bearer token)
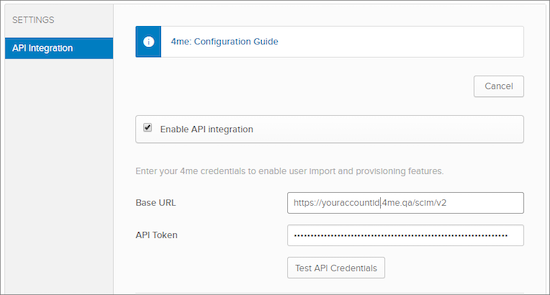
- Test the API credentials
- Save the configuration
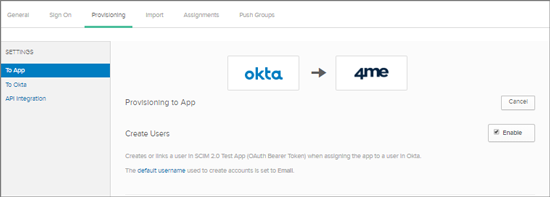
Check the Provisioning to App features
- Go to the Provisioning Section Settings: To app.
- Make sure the following features are enabled: ‘Create Users’, ‘Update User Attributes’ and ‘Deactivate Users’.
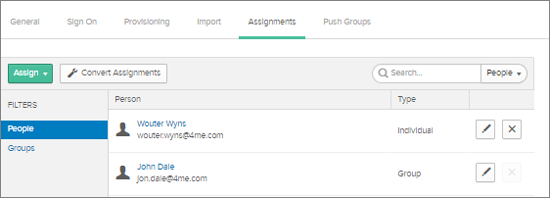
Assign People to Provisioning
You need to assign the people that need to be provisioned to the 4me app. You have the choice to assign individual people records or to assign people based on their group membership.
For people assignments, select ‘People’, search for the people records and Assign them to the App.
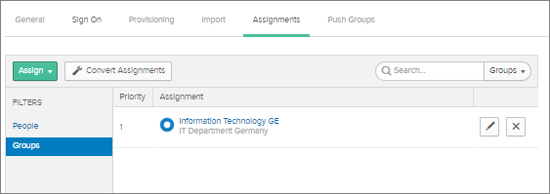
For assignment via Group membership, select ‘Groups’ and search for group records.
When you select a group for provisioning, you are able to define default values for the people attributes like Preferred Language, Time Zone and Cost center.
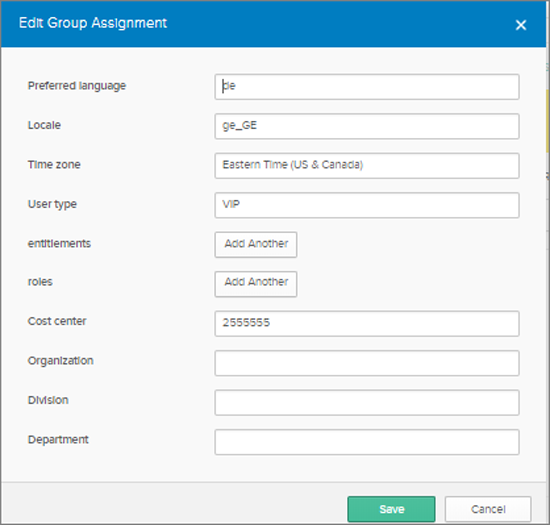
Remark: when you set User type on VIP, the 4me user will have the VIP flag set.
Push Groups
Make sure the right Okta Groups are pushed now to 4me. Goto the ‘Push Groups’ tab, search for the Groups you want to push to 4me and add the Groups to the list.
Schema Discovery
A detailed description of the SCIM Schemas API can be found on the 4me developer site.
Troubleshooting and Tips
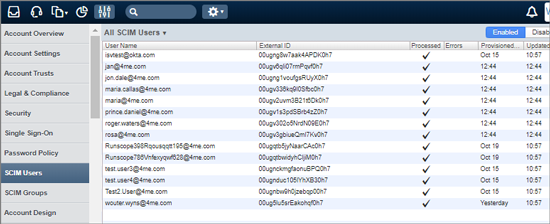
The OKTA users and groups that are provisioned to SCIM, can be found in the 4me account via the Settings console. For each SCIM user and SCIM group that has been provisioned a record is to be found in these lists. You can sort the list on the ‘Provisioned At’ and ‘Updated At’ timestamps. Check for any errors.
Once the SCIM records are created in 4me, they are processed by an automation rule that will update or create the 4me person records. These automation rules implement another layer that you can use to make a correct mapping from OKTA person attributes to 4me person attributes. Click on the Automation Rule execution to check the results of the execution. Click on the Actions button in the header bar to modify the Automation Rules.