Single Sign-On
4me can be configured to use an organization’s existing identity provider (such as Microsoft Active Directory, Microsoft Azure B2C, OneLogin, the Okta Application Network, etc.) instead of 4me’s own authentication mechanism to determine whether a user should be able to access 4me.
By using an existing identity provider, the organization’s 4me users (including the end-users who need to be able to use Self Service) will not require a separate password to access 4me.
SSO Protocol
The following single sign-on protocols are supported:
Using the SSO Configuration of the Directory Account
Support domain accounts are able to use the single sign-on configuration of their directory account. After SSO has been enabled in a directory account, the checkbox ‘Login using SSO configuration of directory account’ becomes available.
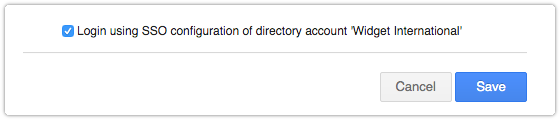
Checking this box hides any SSO protocol specific section. The values for these fields are obtained from the directory account when this feature is in use.
Multiple Identity Providers
When some users are sourced from a different Identity Provider 4me offers the possibility to add multiple SSO Configurations. By default users are redirected to the Primary SSO Configuration on login. Aternative SSO Configurations are accessible using a special Login URL using a reference that you can define in the SSO Configuration form in case multiple SSO Configurations are defined.
Debugging
If SSO has been enabled for a 4me account, but it does not appear to work, then the account owner can access 4me again by adding /access/normal to the URL of the 4me account. Once the owner is back in 4me, the System Logs section of the Settings Console can provide some useful information about why SSO is not working. Whenever there has been an authentication failure, an entry will have been added to the log with an explanation of what went wrong.
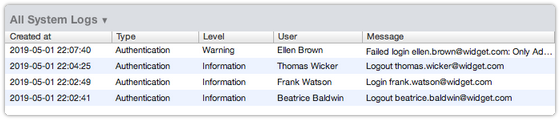
Also keep in mind that the clock of the servers of the identity provider need to be synchronized. If the clock is more that 2 seconds out of sync, the response from the identity provider will not be accepted by 4me.
If SAML is the protocol used, then another useful source of information is the SAML meta data.