Single Sign-On - OpenID Connect
4me can act as a relying party that requests user authorization from an OpenID Connect Provider.
OpenID Connect Single Sign-On Transaction Steps
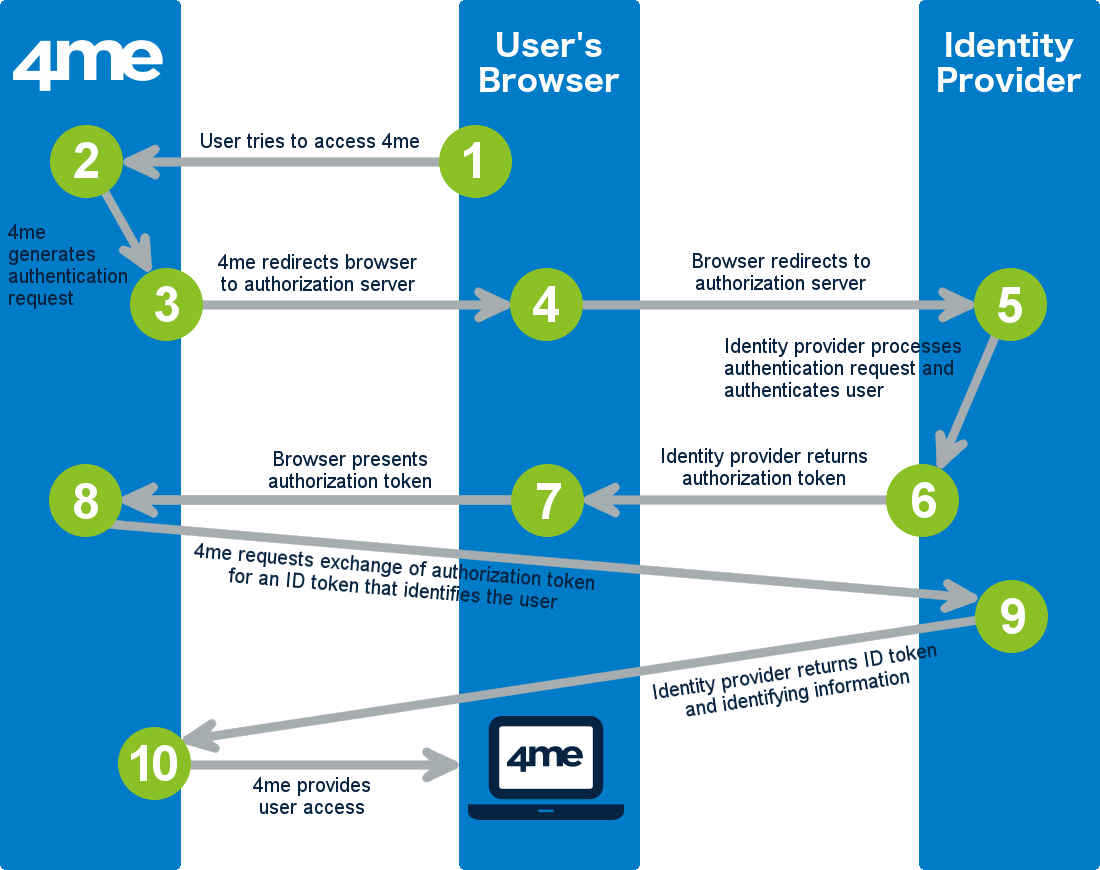
The image above illustrates the following 10 steps that complete one OpenID Connect SSO transaction:
-
The user attempts to access the 4me account of his/her organization using a browser application such as Microsoft Internet Explorer, Google Chrome, etc.
-
4me looks up the settings of the 4me account of the user’s organization and sees that SSO has been configured in this account. That is why, rather than prompting the user for an email address and password, 4me generates an OpenID Connect authentication request. 4me then encodes this authentication request and embeds it into a redirect URL that is intended for the SSO service of the identity provider that the user’s organization uses.
-
4me sends the redirect URL to the user’s browser.
-
The user’s browser redirects to the identity provider’s SSO service.
-
The identity provider processes the authentication request. This means the identity provider will ask the user to authenticate. If this is the first time the user is asked to authenticate to access 4me the user may be asked by the identity provider to provide consent that 4me is allowed to view user information such as name and email address.
-
Once the user has provided consent and has authenticated, the identity provider generates a response that contains an authorization token.
-
The user’s browser forwards the authorization token to 4me.
-
4me sends a request directly to the identity provider (bypassing the user’s browser), requesting the identity provider to exchange the authorization token for an ID token that identifies the authenticated user.
-
The identity provider returns an ID token and other identifying information.
-
4me validates the response and checks it against (amongst others) CSRF and replay attacks. If the ‘Allow JIT provisioning’ field is enabled for the SSO configuration of this account, the JIT End User Access Provisioning functionality is triggered to automatically generate a new person record if one does not yet exist with the user’s email address, or to automatically update the user’s person record in 4me.
After that, 4me redirects the user to the destination URL within the 4me account of the user’s organization. The user is now logged in to 4me.
How to Enable OpenID Connect SSO for 4me
To make OpenID Connect SSO work for an organization’s 4me account, the 4me account owner will need the following information:
-
the Client identifier
-
the Client secret
-
the Issuer identifier
This information can then be entered by the 4me account owner in the Single Sign-On section of the Settings console.
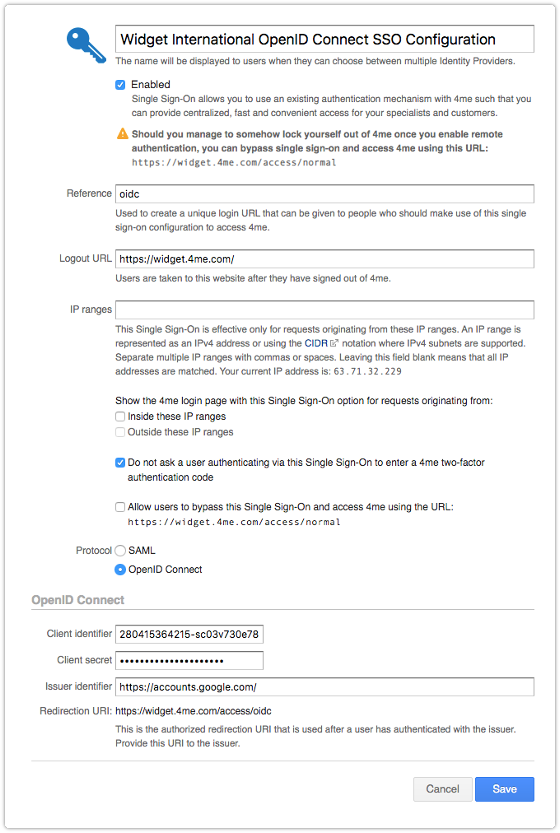
Once SSO has been enabled, the account owner can check whether it works by logging out of 4me and subsequently trying to access 4me again by going to the URL of the 4me account. If the account owner is already logged in to the identity provider, 4me nor the identity provider should no longer ask for an email address and password. Instead, the account owner is directly taken to the 4me inbox.